Legal compliance vs. device security in the real world

This article summarizes the main points from Terry London’s speech at the trade event, Embedded World 2025. Drawing on his experience at Proekspert, Terry explains how the EU Cyber Resilience Act will affect industrial device security, outlines practical steps for compliance, and highlights best practices for balancing security with business needs.
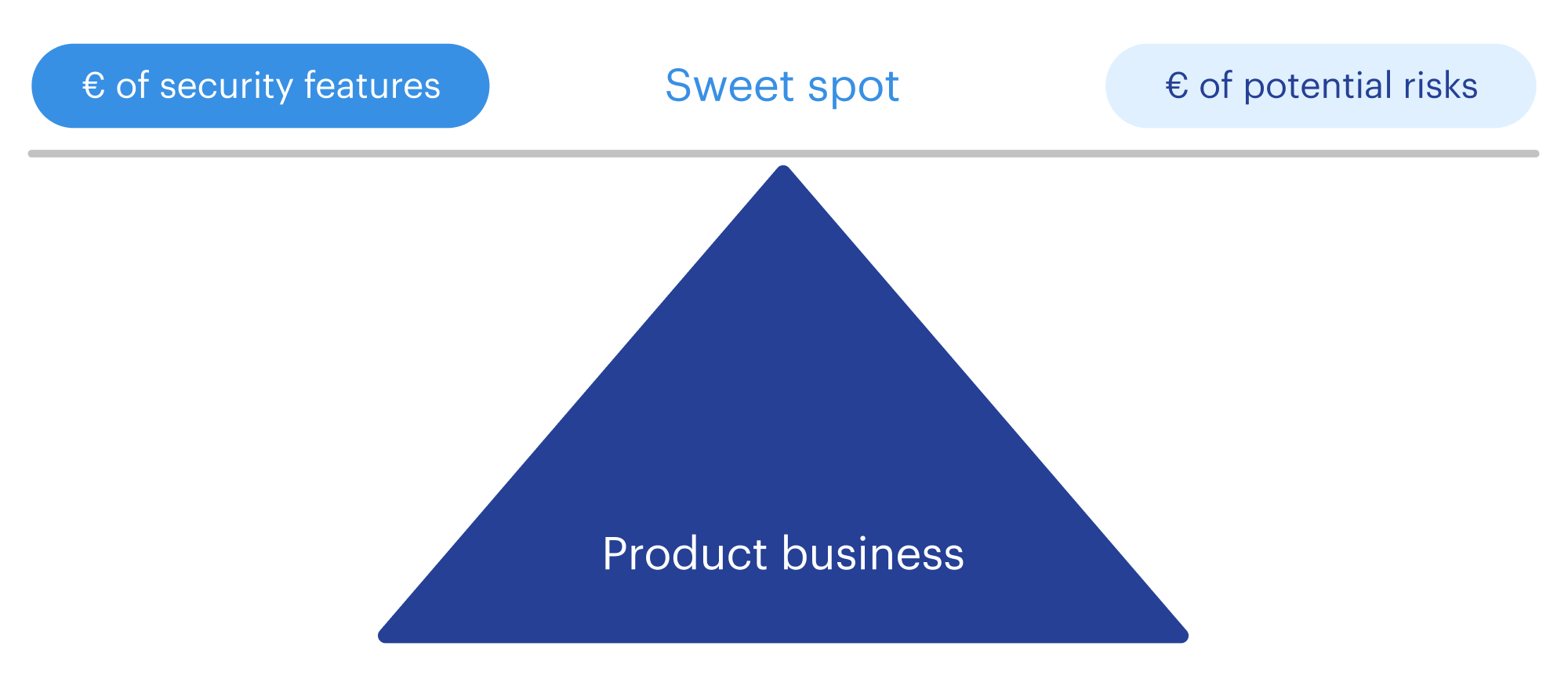
To avoid pitfalls in device cybersecurity implementations, begin with a comprehensive risk assessment to identify the optimal balance between investment and outcome when building cybersecurity equipment.

The use of digital technology in manufacturing has changed how factories work. Automation, connected systems, and quick data analysis are important for success. At the same time, keeping these digital products secure and reliable is more important than ever, especially as new rules are introduced for industrial automation.
Understanding the EU Cyber Resilience Act
The European Union’s Cyber Resilience Act (EU CRA), released in December 2023, is a landmark regulation designed to strengthen cybersecurity for all products containing digital elements. Set to take effect in December 2027, it gives businesses a little over two years to adapt—the blink of an eye in complex R&D cycles.
At Proekspert, we’ve already observed the effects of the upcoming act, impacting not just new development, but also forcing updates to longstanding products. Industrial device manufacturers now face crucial decisions on how to meet these new requirements without upward spiraling costs or introducing unnecessary complexity.
Balancing security and business needs
Security comes at a price, and adding it later or doing it without proper planning can end up costing much more. The key is to make thoughtful business and engineering decisions from the start.
We’ve seen instances where ambitious security goals dictated by management led to excessive costs or features that failed real-world usability tests. The lesson? Security must serve both compliance requirements and the end-user experience. Ultimately, security is of little value if it makes products unusable or uncompetitive.
Demystifying the EU CRA
The EU CRA is not just another directive by the EU, it’s a binding regulation that covers all products with digital components sold in the EU. If your product carries a CE marking, it will almost certainly be affected. The Act enforces risk-based security measures, with a strong focus on protecting end users and maintaining transparency across product lifecycles. From a market perspective, compliance isn’t just about ticking boxes—it can give customers confidence, differentiate products, and drive business success.
In practice, the EU CRA requires manufacturers to:
1. Follow essential cybersecurity requirements and conduct cybersecurity risk assessments.
2. Set policies and processes to report on and handle vulnerabilities, including the Software Bill of Materials (SBOM).
3. Perform conformity assessments according to product class.
4. Report exploited vulnerabilities and incidents promptly and transparently.
5. Provide security updates for as long as a product is supported, a minimum of five years.
Begin with risk assessment
The first and most crucial step toward compliance is a comprehensive cybersecurity risk assessment. This process involves:
- Mapping all use cases and foreseeable environments.
- Identifying vulnerabilities and critical data flows.
- Evaluating the balance between usability, security, and cost.
- Documenting which essential requirements and standards (such as IEC 62443) apply.
For industrial devices, legacy complexity only adds to the challenge. Products may have been developed over decades with intricate codebases and unpredictable interdependencies. Risk analysis helps navigate this complexity intentionally, rather than reactively.
Best practices for compliance
Start with analysis: Assess and understand realistic risks before prescribing security features.
Prioritize usability and business goals: Choose security measures that are sustainable and aligned with how your clients actually use your products.
Plan for the product lifecycle: Cybersecurity isn’t a one-off; it must be maintained, updated, and verified as technology and threats evolve.
Supporting our customers
Our core mission at Proekspert is developing secure systems—EU CRA compliance is now seamlessly built into our process. We specialize in:
- Guiding clients through self-assessment and gap analysis (especially with IEC 62443).
- Establishing processes for vulnerability reporting and SBOM maintenance.
- Implementing tailored security update mechanisms.
We work directly with our clients’ engineering teams, ensuring security investments are reasonable and effective, avoiding unnecessary costs and complexity. Proekspert helps clients integrate these practices into their core development processes, from initial architecture to post-launch support.

Final thoughts
The EU CRA represents both a challenge and opportunity for industrial device manufacturers. By approaching it as a chance to build better, safer products—balanced for real-world use—you can not only comply but excel.
About Proekspert
Proekspert is a skilled software development company with over 30 years of experience. We have encountered many diverse approaches to equipment, software engineering, and cybersecurity. Our expertise covers embedded software, device-cloud integrations, technician apps, and portals.
About Proekspert
Proekspert is a skilled software development company with over 30 years of experience. We have encountered many diverse approaches to equipment, software engineering, and cybersecurity. Our expertise covers embedded software, device-cloud integrations, technician apps, and portals.









