A secure firmware update solution
Device security
Cloud connectivity
Apps and portals
Proekspert helps device manufacturers to prepare for upcoming EU Cyber Resilience Act
We develop secure firmware update solutions that ensure the device software is protected no matter how the update package is delivered to the device: over-the-air (OTA) or wired medium.
Register here for free meeting where we help you to discover how to improve your device security.
The secure firmware update solution is used in three case scenarios.
S1. Preventing unintended device firmware updates
Updating devices over the internet or on-site by a technician poses risks of malicious usage and simple human error and may render a device inoperable, causing enormous expense, especially when the device is in a difficult to reach or remote location. To give device manufacturers more control in the software update process, Proekspert has developed a hardware-level device firmware authenticity validation solution.
S2. Licensing device firmware
Device makers need control over software that is run on their devices. Proekspert has developed a hardware-level license verification solution to determine if an end-user is eligible for software updates or new features.
S3. Protect device firmware for industrial espionage
Common risks when updating device software
Unverified sources
Offline devices cannot verify if the specific firmware image is coming from an authentic source
Lack of trained specialists
Updating device software manually on site is costly for maintenance service providers
Malicious users
Malicious users may tamper with the device by altering the original firmware update package
Unintended features
Wrong firmware version may ruin the user experience or break important features
Key features and benefits of our solution
Enabling secure remote updates Over-the-Air and via Ethernet
Preventing human errors by protecting a device against manual invalid FW updates online and offline
Protecting device software against malicious usage and network attack
Enabling device-level software licenses
How it works
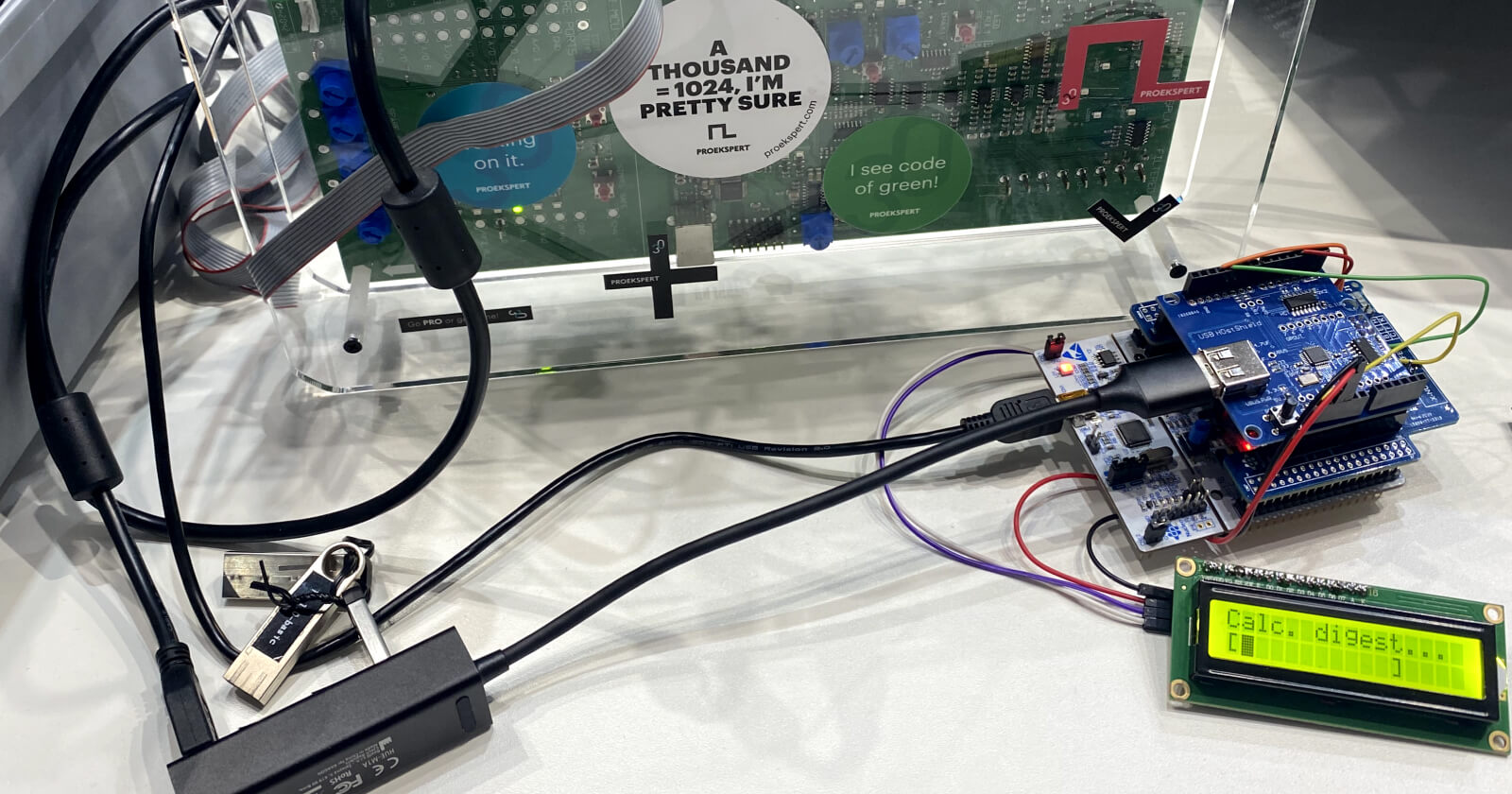
Proekspert’s firmware authenticity verification software uses a crypto processor chip (TPM) integrated with a device’s motherboard to automatically verify an update file signature and/or decrypt a previously encrypted firmware update package. Each TPM is unique, so on the device software development side the firmware is signed or encrypted for devices one by one. When a device updater discovers firmware with an incorrect signature or encryption, the update process halts without altering already installed software.
Secure FW update from a cloud service

Get the solution brief
Discover how Shield-loT enables organizations to monitor and secure any loT device, application and network
Get in touch
We have tens of years of experience in developing secure software by design. Keeping the balance between security and end-user experience is a common practice for us.
Leave your contacts below, and let's have a quick online call to see if we are the right partner for you to prepare your devices and infrastructure for CRA.
Thank You!
Your message has been sent. Our team will get back to you as soon as possible!
Jukka Antero Halttunen
Why Proekspert?
Proekspert has comprehensive expertise in developing custom industrial device security solutions. For 30 years we have helped our clients develop device security and update solutions. In addition of building custom firmware update solutions we are experienced in using over-the-air (OTA) and various industrial communication protocols and mediums.
It’s crucial to strike a balance between security and usability. By following best practices, integrating security early in the development process, and considering user experience, you can prepare for the CRA while ensuring your devices remain usable and efficient.
If you’re looking for an experienced embedded software solutions development partner to improve your device security, feel free to contact us.