Cyber security: why it shouldn’t be an add-on
In the tech world, the standard approach to cyber security is to develop first and protect later—here’s why that model is both wrong and dangerous.
In this era of cyber attacks and ransomware, security is on everyone’s mind. We tend to rely on platforms, frameworks, and cloud providers to ensure the security of our information, but can we trust these solutions?
What is cybersecurity, in simple words?
Cybersecurity involves safeguarding systems, networks, and programmes against digital attacks. These attacks often seek to steal, alter, or delete critical data, extort money through ransomware, or disrupt normal business activities.

How we approach cyber security and why
At Proekspert, we always say that putting a powerful lock on a paper door won’t make a cardboard house secure. Indeed, this is the perfect metaphor to describe the approach widely used today.
Perhaps it is high time we reinvent our approach to cyber security.
Regarding security, countless companies will try to sell you a one-fits-all solution. Their offer might be security as a service, high-quality penetration testing, or log analysis for finding outlying incidents and anomalies. While they may seem compelling on paper, none of these solutions work in the real world because security comes down to people, behaviour, and the processes and standards you have in place. Different kinds of software can help and assist you in ensuring the security of your data, but they will never do the work for you.
How many companies, in a variety of spheres, implement security is not perfect either. Considering how quickly circumstances change in the world today, it is understandable that no one seems to have the time to document, plan, or consider theoretical security aspects if features are not ready and the MVP is not delivered. Most importantly, security and privacy requirements are left out of the MVP. Only when design and development are complete do we consider talking to the security team and ask for their final sign-off.
An approach of this kind is fundamentally flawed: we build a house with a paper door, and when the product is almost finished—its launch date due—we ask the security team to put their best, most secure lock on that paper door, leaving no time for a deeper analysis. Moreover, in that final phase, any fundamental change would delay the project and be extremely costly.
Types of cyber security threats
What is a tailgating attack?
Tailgating is an attack in which an unauthorised individual gains access to a restricted area, such as a password-secured zone, potentially to steal confidential data, harm property, obtain user credentials, or introduce malware onto computers.
‘Piggybacking’ resembles tailgating but includes an employee’s unwitting consent. In this scenario, a hacker, possibly masquerading as a delivery driver, convinces an employee to grant access, unlike tailgating, where the employee remains unaware of the breach.
What is a phishing cyber attack?
Phishing is a cyber-attack where malevolent actors send deceptive messages, posing as credible individuals or organisations. These messages coax users into actions like downloading harmful files, clicking dangerous links, or revealing sensitive details like login credentials.
Phishing, a prevalent form of social engineering, involves manipulating or deceiving computer users. This tactic, a growing threat in many security incidents, often pairs with other dangers like malware, code injection, and network attacks.
Using different cyber security tools
Using different cyber security tools, services, or penetration tests is undoubtedly helpful, but there is much more you can do and many more measures you, as a company, should take.
Perhaps you are wondering, what exactly would be a better approach?
Unfortunately, there are no foolproof answers. But having extensive expertise in this field, Proekspert can provide at least the beginnings of a comprehensive solution.
Above all else, we would advise an approach wherein security and privacy are planned and designed for—not dealt with as an afterthought or the final stage of development.
What does security by design look like?
Well, first of all, it means onboarding security analysts as early as possible with projects, even if a project is still in its whiteboard-drawing phase. When security is factored in so early on, changes and preventive measures are easy to make and way more cost-effective.
What is cyber security software, and how do we use it?
Cyber security software, designed to thwart complex cyberattacks, frequently integrates various tools like machine learning and AI solutions for dynamic protection against constantly emerging threats. Additionally, it ensures resilience in case of successful attacks by safeguarding email, backing up vital data, and maintaining business continuity.
At Proekspert, we ensure our software is also designed with security in mind.
You will never be able to eliminate all bugs before a release. Still, you can avoid as many errors as possible before the final version goes out and penetration testing begins. During the development process, it is best to practice threat modelling (more on this in our next article) and systematically identify weaknesses and attack vectors. This way, you can prepare for the worst and develop solutions for your product.
What is a Security Development Lifecycle, and why do we use it?
The Security Development Lifecycle (SDL) consists of practices supporting security assurance and compliance requirements. The SDL helps developers build more secure software by reducing the number and severity of vulnerabilities.
If your company has not yet implemented any Security Development Lifecycle, we recommend that you experiment with the Microsoft model and then adjust it to your company’s needs.
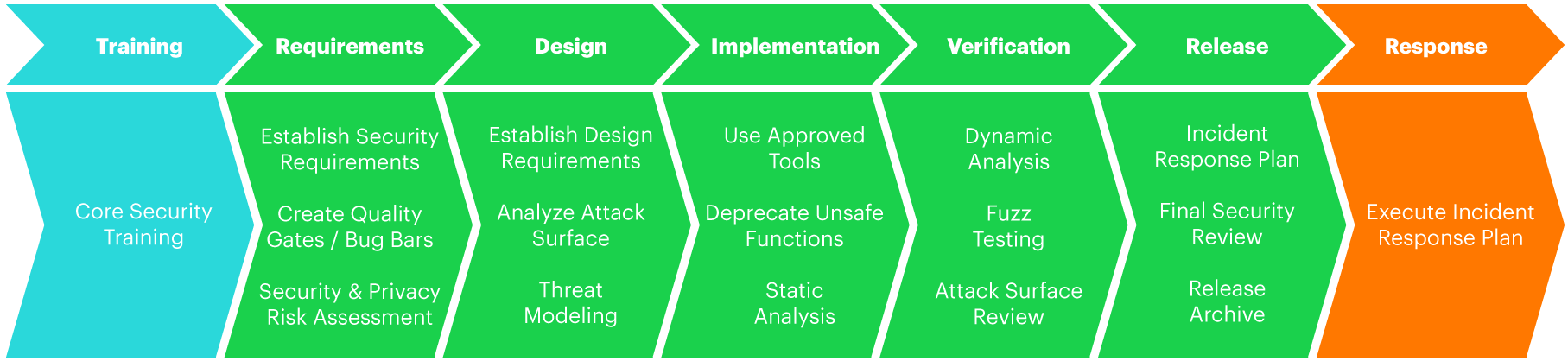
But if you are eager to look at other best practices on creating a custom SDL, we suggest that you also take a look.
After implementing a suitable SDL and integrating security analysis within earlier stages of your design process, you can still take several measures to ensure security. Here are just a couple:
- Train your developers regularly to ensure that the majority understand the most common attacks, defence mechanisms, etc. This may be time-consuming, but as long as attacks change, so must protection mechanisms. Your team must be on top of the latest trends.
- Make sure you have a dedicated security team that can assist with design and architecture, conduct penetration testing, give general advice, and work on research to help product teams deliver secure software.
- Try to implement a plan to ensure that protection is cheaper than any potential loss. Create a system where some services can be taken down in case of critical incidents without causing any disruption to business. At the same time, mission-critical systems need the best possible security you can implement.
Regarding software, there are no foolproof solutions and no 100% guarantees against hacking. Critical bugs are bound to go around, and they may not even happen in your code but in the library or service code that you are using.
It is impossible to mitigate everything, so you must consider these risks in your threat model, acknowledge them, and prepare for their eventual occurrence—no matter how unlikely.
Assessing cyber threat risks
A cybersecurity risk assessment involves assessing threats to your organisation’s IT systems and data and your ability to protect these assets from cyber attacks.
Organisations can (and should) use a cybersecurity risk assessment to identify and prioritise opportunities for improvement in existing information security programs.
A risk assessment also helps companies communicate risks to stakeholders and make educated decisions about deploying resources to mitigate those security risks.
Managing your cyber threat risks
Every organisation using IT infrastructure must perform cybersecurity risk assessments. However, limited resources can hinder small businesses from thoroughly evaluating and mitigating risks. Consequently, many turn to cybersecurity software for enhanced evaluation, mitigation, and monitoring of their risk management strategies.
Modern cybersecurity solutions focus on threat intelligence to guard against the three primary cyber risk categories: malware, ransomware, and phishing.
But why is understanding and mitigating cybersecurity risk so important?
It’s all about assessing and managing risk. If you ignore potential problems, and then one day they begin to flare up, you might discover that you are unprepared:
- You don’t have logs.
- You don’t have abuse-detection mechanisms.
- You don’t have any protocols for properly identifying and analysing an attack.
That’s precisely the kind of situation all companies should try to avoid.
Security takes time and effort, but it is always worth it.
Contact us if you want to ask for advice about the security of your digital products.












